Empowering Businesses
with End-to-End IT Managed Services
Accelerate | Beat Competition With IT Managed Services for SMEs
Free up your time and resources to focus on what you do best while we handle your IT infrastructure management and cybersecurity consulting needs.
YOUR ALWAYS-ON BUSINESS DRIVER
Your Digital One-Stop-Shop – we’ve got it all covered:
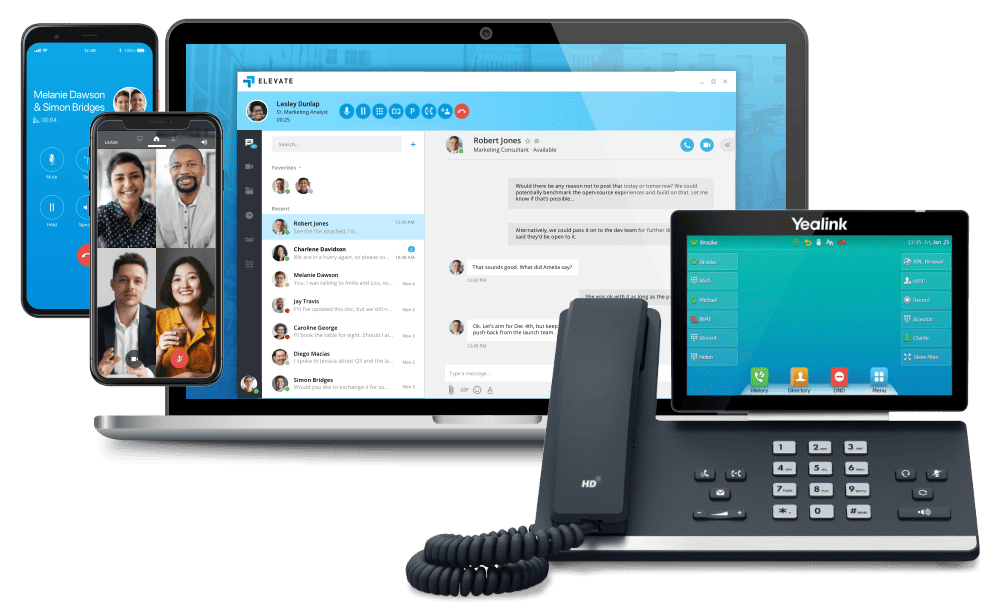
SIMPLIFY YOUR CUSTOMER COMMUNICATION
Stop missing your customer calls with premium cloud based unified business communication services at a fraction of your current cost.
Book a free IT risk assessment and discover how our One-Stop-Shop Managed IT services for SMEs, Cybersecurity, Business Communications and AI can drive your business forward. Contact us today whether in Surrey or looking for a comprehensive IT support in White Rock, Burnaby, Langley or across BC.
your success My Passion
By combining 20+ years of IT experience with my global insights and profound love for our vibrant local communities, I set out to create OLAYEMIS – not just as a Managed Service Provider, but as a committed partner to local businesses, helping them to thrive in an ever-evolving digital world.

Before You Switch IT Support – Read This First!
In a world where technology is your backbone, the right IT support or Service provider isn’t just an option – it’s your lifeline. Your choice in IT support can empower your team to soar or leave them entangled in tech troubles.
Recent times have revolutionized our dependence on technology, making a competent IT partner not just beneficial but essential. That’s why we’re swamped with inquiries from businesses rethinking their IT strategies.
Partners





RESOURCES
- A third of all data loss is caused by problems with backups
 Your business data is backed up and recovery tools are in place. So, your data is safe, right? Sadly… not always. Here’s why we recommend backups are checked regularly..
Your business data is backed up and recovery tools are in place. So, your data is safe, right? Sadly… not always. Here’s why we recommend backups are checked regularly.. - Reverse image search makes purchasing and marketing easier
 Think the Windows 11 Photo app has little use in your business? Visual Search with Bing is about to change that, with some very useful new functionality… Find out more here.
Think the Windows 11 Photo app has little use in your business? Visual Search with Bing is about to change that, with some very useful new functionality… Find out more here. - A free tool for more polished communication
 You’ve hit send on an important email – then you notice a typo. Windows 11 lets you spellcheck and autocorrect across most of its apps. Here we help you to set it up
You’ve hit send on an important email – then you notice a typo. Windows 11 lets you spellcheck and autocorrect across most of its apps. Here we help you to set it up
We have a whole library that will give a better understanding of IT and Cybersecurity.